1. Fingerprint recognition

Fingerprint-based identification involves looking at the surface of the finger for special features in the line pattern. The splices, endpoints and islands that form this line pattern are thereby stored as an image.
The disadvantage of an image with external features is that it can be replicated. Even if stored encrypted. An image remains an image and can therefore be compared, after which you can basically generate the same code. ‘Spoofing’* of fingerprints is already possible with relatively low-threshold technology. Last but not least, a finger presented for recognition doesn’t necessarily needs to be attached to a body anymore…
There are also line patterns that are so similar that, in practice, this leads to a high false acceptance rate.** In addition, fingerprints can wear off; as you get older or as a result of the work you do. As a result, some fingerprints may not be recognised (false rejection**) or may not even be registered. There is even a known hereditary condition that causes people to be born without a finger line pattern(!)
On the other hand, fingerprint-based identification is already known to a wide public, so the method is accepted by many users. The technology is also relatively inexpensive and easy to use. But beware: there are major quality differences between different fingerprint recognition systems, with false acceptance rates and false rejection rates varying enormously.
* Biometric spoofing is offering a falsified biometric to be identified as someone else. This can be something like a counterfeit fingerprint or a contact lens with a fake iris pattern. Spoofing poses a particular risk with forms of biometrics based on superficial external characteristics.
** Read more about false acceptance and false rejection in our article ‘FAR en FRR: security level versus ease of use’.
2. Facial recognition

Facial recognition looks at the extent to which parts of the face match in terms of shape, position and location. Sometimes this also involves paying attention to surface features, such as the skin.
The use of facial recognition for security purposes stems from the deployment of face detection technology: searching for faces in more complex images, which may contain multiple faces. As this technology has developed significantly in recent years, it is a prime candidate for remote recognition. Another plus of the technique is ‘negative identification’, or excluding faces. This makes it a lot easier to scan a crowd for suspicious individuals.
However, facial recognition also has some significant drawbacks. For instance, the technique usually focuses on the face itself, i.e. from the hairline. This usually requires looking straight at the camera to enable recognition. And although the technology is still under development, the level of security so far is not comparable to that of iris scanning or vein pattern recognition.
3. Iris recognition

In an iris scan, a scanner reads the unique characteristics of an iris, which are then converted into an encrypted (bar) code. Iris scanning is known as a very good security technique, especially if it is done using infrared light.
However, a common problem in implementing the technology is user resistance. Quite a few people find it very annoying to have their eyes scanned. People with eye conditions in particular may find the beam of light in their eyes uncomfortable. In addition, one has to adopt a certain posture for the scanner to read the iris, which can cause discomfort. Hygiene is also often cited as an objection, as many systems require users to place their chin on a holder. The same holder that has been used by so many people before.
Finally, it is important to realise that security using an iris scan may come at the expense of speed. Incidentally, systems that can read the iris from a (limited) distance have recently come to exist.
4. Finger vein pattern recognition
 In recognition based on vein patterns, the endpoints and branches of the veins in the finger are captured as images, digitised and converted into an encrypted code. That, and the fact that veins are not on the surface of the skin but underneath, immediately makes this technique much more secure than fingerprint-based identification. It also works faster and is even easier to use. However, the method is more expensive.
In recognition based on vein patterns, the endpoints and branches of the veins in the finger are captured as images, digitised and converted into an encrypted code. That, and the fact that veins are not on the surface of the skin but underneath, immediately makes this technique much more secure than fingerprint-based identification. It also works faster and is even easier to use. However, the method is more expensive.
Also something to keep in mind: very cold fingers and ‘dead’ fingers (e.g. in the case of so-called Raynaud’s syndrome) cannot be read (properly) using finger vein pattern recognition. But perhaps the biggest drawback is that this technique is still relatively unknown.
5. Palm vein pattern recognition
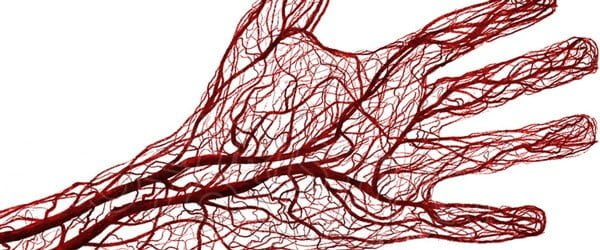 This technique is also based on recognition of unique vein patterns. But because this occurs at even more reference points than vein pattern recognition in the finger, palm vein pattern recognition is an even safer and simpler means of identification. The technique, which is very difficult if not impossible to copy, is currently considered the best available method in biometric security, along with iris recognition. Palm scanning works quickly and accurately, and the ease of use is great.
This technique is also based on recognition of unique vein patterns. But because this occurs at even more reference points than vein pattern recognition in the finger, palm vein pattern recognition is an even safer and simpler means of identification. The technique, which is very difficult if not impossible to copy, is currently considered the best available method in biometric security, along with iris recognition. Palm scanning works quickly and accurately, and the ease of use is great.
Access control based on the vein pattern in the palm of the hand is a very secure system. As a result, it is mainly used within industries with high security requirements, such as the government, judicial and banking sectors.
Note: it is still sometimes the case that this form of recognition is confused with hand geometry. However, that is an outdated form of biometrics, which is based on the shape of the hand and has even fewer unique features than the fingerprint. Want to know more or looking for a biometric security solution for your organisation?
